The use and management of information security is a key to ensure the confidentiality of information processed by entities element, and on the other hand the availability of the same in the format, medium, and time required. Our service is based on the methodologies defined by the Management System Information Security (ISMS) and the main safety regulations Information: ITIL, COBIT, ISO 17799.
Services – Information Security

Our Information Security Consulting Service is based on the principles of action defined by the Information Security Management System (ISMS).
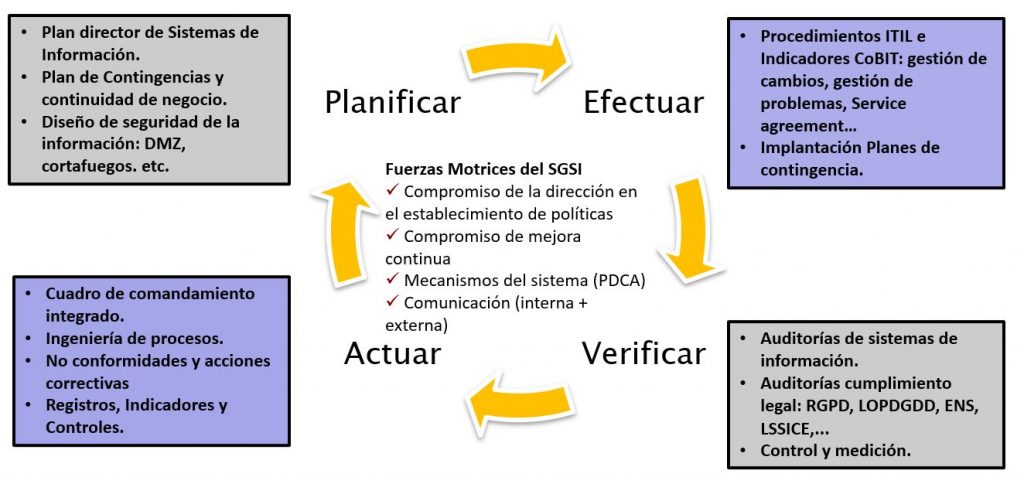
If the company has a sufficient level of maturity, the documentation, adaptation and certification tasks are carried out according to the ISO / IEC 27001_2013 standards.

Information Security Audit: focused on information security in its different areas.
- Processes: Guarantee that information is processed with security throughout the Life Cycle, from acquisition to destruction or Archiving.
- Organizational: Guarantee the profile access, training and information process of internal personnel and third-party companies are correct.
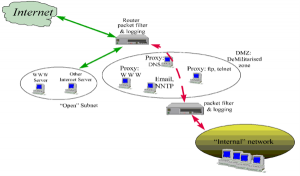
- Technique: Design and configuration of computer systems, communications networks, etc. including a security assessment based on the use of ethical hacking techniques (Ethical hacking)

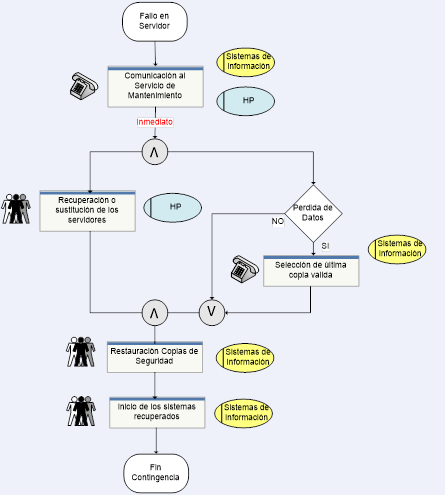
Definition of alternative means and precise procedures to be applied by the entity in the event that one or several services or key business processes are not available for the execution of the business in order to guarantee the continuity of the services.
They are mainly carried out:
- Identification of the IT assets, procedures and key roles that support the services related to the execution of business processes and procedures.
- Identification and classification of potential risks.
- Determination of alternative means and resources in the event of a risk materializing.
- Preparation of technical and organizational documentation: protocols, procedures and contingency plans